Mutual Authentication
Mutual Authentication allows the device and Everyware Cloud to authenticate each other over certificate-based TLS/SSL Two-Way Authentication protocol. This feature is supported for the MQTT connections established by the devices to the Messaging Service of Everyware Cloud.
The connection will succeed if, and only if:
- The backend holds a certificate that is trusted by the device
- The device holds a certificate that is trusted by the backend
- The device credentials, username and password, used to establish the MQTT connection are successfully validated by the backend
Mutual Authentication increases the level of security of the communications between the devices on the field and Everyware Cloud in the backend providing protection against several adversarial attacks.
Everyware Cloud Mutual Authentication is designed to provide the maximum control over device authentication. With a simple action from the Admin Console (or from the RESTful API) a user can enable/disable the authentication of the devices changing the status of one or more public key certificates in Everyware Cloud own Certificate Service. The granularity of the control spans from the single device up to the whole fleet of devices within the account.
Enable Mutual Authentication
Mutual authentication needs first to be enabled at the account level. In the In the Settings view select the ClusterService and check whether the TLS/SSL Mutual Authentication connections are enabled.
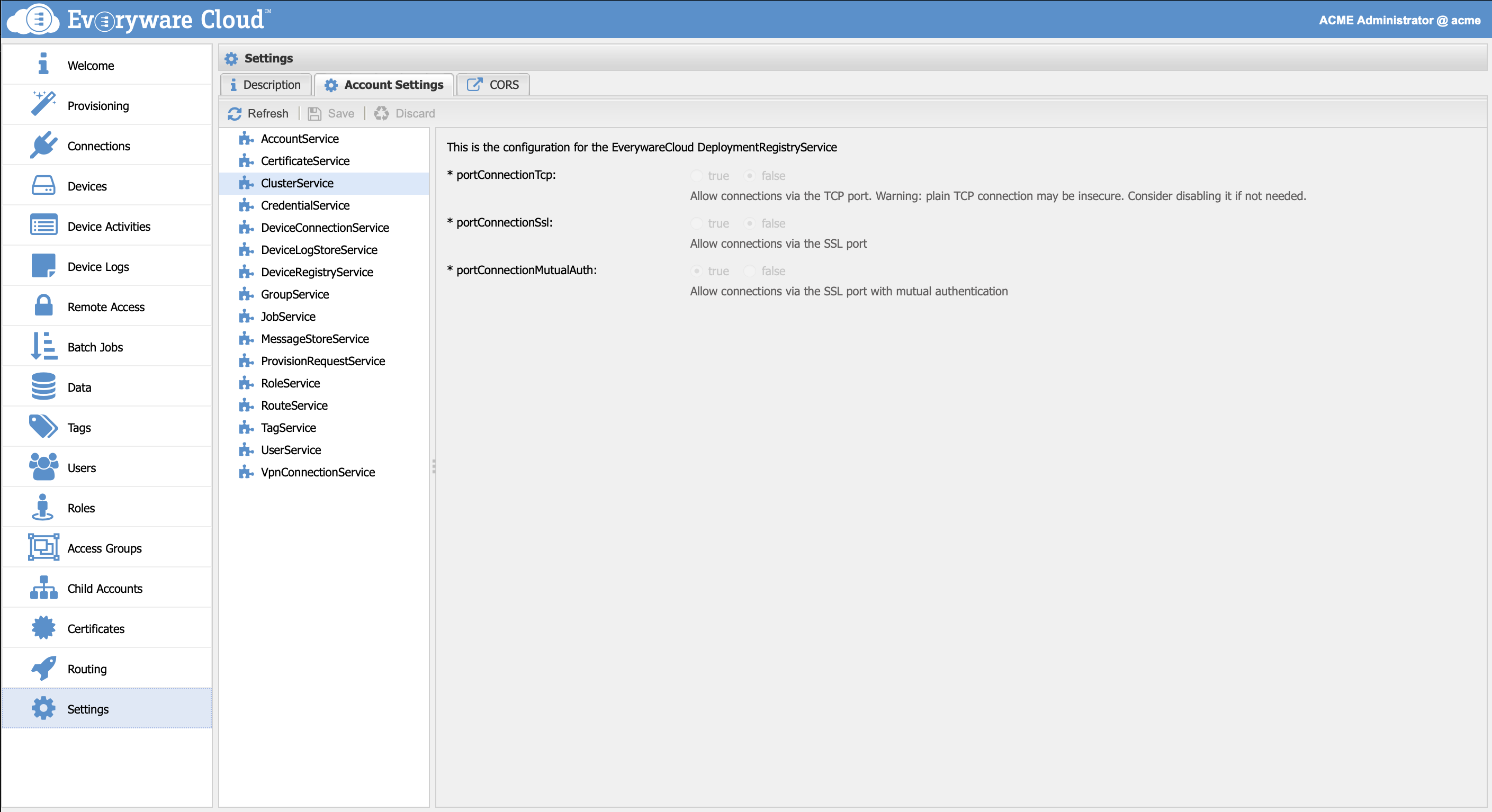
If the option for the Mutual Authentication is disabled, contact your account provider.
Multiple Options Enabled
When both SSL/TLS and SSL/TLS with Mutual Authentication are enabled, Everyware Cloud will try first to establish a mutually authenticated connection (by validating the certificates sent by the device) and then fallback to plain SSL/TLS connection if the attempt fails.
Configure Device Authentication
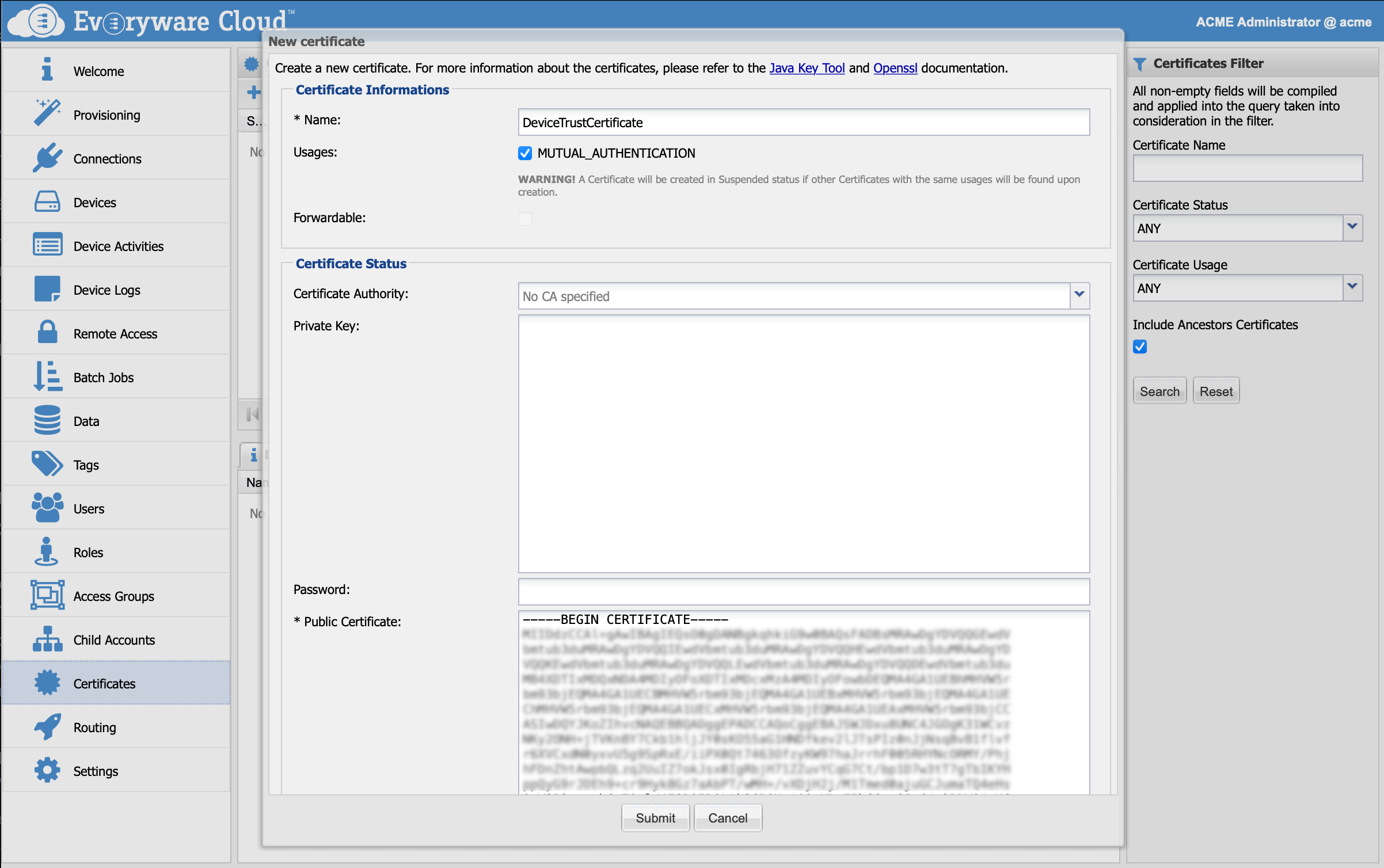
To let Everyware Cloud authenticate the device through Two-Way TLS authentication, it has to have a public key certificate that can validate the client certificate. This certificate can be a leaf certificate, an intermediate certificate or the root CA, installed in the top-level account. In the Admin Console, go to the Certificates view and click the Add button. A new dialog will appear to allow the registration of a new certificate. The mandatory fields are:
| Field | Default Value | Description |
|---|---|---|
| Name | empty | Display name for the certificate |
| Usage | unchecked | select MUTUAL_AUTHENTICATION |
| Public Certificate | empty | BASE64 encoded Certificate, including the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- tags |
Device Configuration
To configure Mutual Authentication in an ESF device, please refer to ESF Documentation, or refer to this example for a plain Paho client.
Verify that the device trusts the TLS/SSL server certificate configured for the Everyware Cloud Messaging Service.
Revoke or Suspend Device Authentication
Connection attempts from a device can be blocked by suspending or revoking the public key certificate used by Everyware Cloud to authenticate. When a certificate gets suspended or revoked the messaging service will no longer accept new connections from the device.
In the Admin Console, go to the Certificates view. Select the certificate and click the Edit button. Select whether to suspend or revoke the certificate.
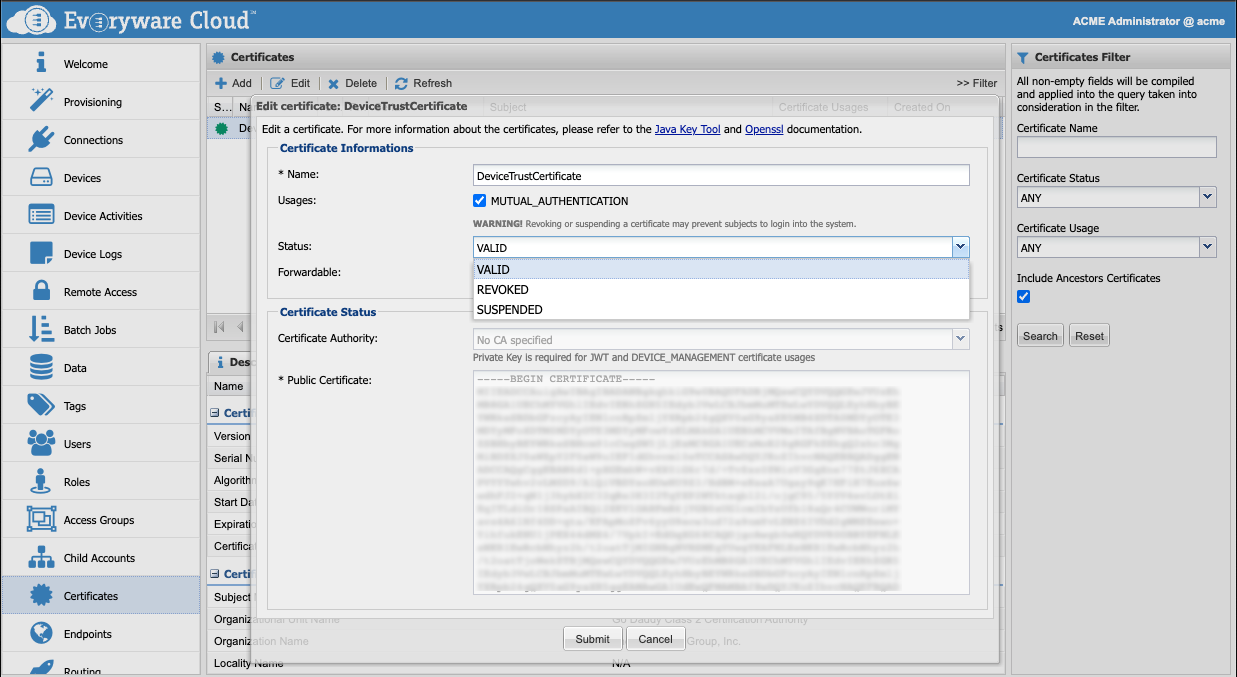
The distinction between the two states is logical. A certificate is suspended when it is temporarily invalid. A certificate is revoked when it is permanently invalid.
Suspension and revocation of the validity of a device is local to Everyware Cloud and the information is not shared with external services.
Certificate status can be changed at any time by the user so a device that is revoked can be turned to valid or suspended.
Integration with external PKI Services
Everyware Cloud RESTful API can be used to build integration with external PKI services to create/suspend/revoke device certificates.
Updated 4 months ago
